ConnectWise, which offers a self-hosted remote desktop software application widely used by managed service providers (MSPs), warns of an unusually sophisticated phishing attack that can allow attackers to take control of users’ systems remotely when recipients click on the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.
A phishing attack targeting MSP customers using ConnectWise.
ConnectWise Control is extremely popular among MSPs who remotely manage, protect and maintain large numbers of computers for client organizations. Their product provides dynamic client software and a hosted server that connects two or more computers together and provides temporary or persistent remote access to those client systems.
When a support technician wants to use it to remotely administer a computer, the ConnectWise website generates an executable file that is digitally signed by ConnectWise and downloadable by the customer via a hyperlink.
When the remote user needing assistance clicks on the link, their computer is then directly connected to the remote administrator’s computer, who can then control the customer’s computer as if they were sitting in front of it.
While modern Microsoft Windows operating systems by default ask users if they want to run a downloaded executable file, many systems configured for remote administration by MSPs disable this User Account Control feature for this purpose. particular application.
In October, security researcher Ken Pyle alerted ConnectWise that its client executable is generated based on parameters controlled by the customer. This means that an attacker could create a ConnectWise Control client download link that would bounce or proxy the remote connection from the MSP servers to a server controlled by the attacker.
This is dangerous because many organizations that rely on MSPs to manage their computers often configure their networks so that only remote support connections from their MSP’s networks are allowed.
Using a free ConnectWise trial account, Pyle showed the company how easy it was to create a client executable that was cryptographically signed by ConnectWise and could bypass these network restrictions by bouncing the connection. via an attacker’s ConnectWise Control server.
“As an attacker, you have full control over the link parameters, and that link is injected into an executable file downloaded by the client through an unauthenticated web interface,” said Pyle, partner and exploit developer at Cybir security company. “I can send this link to a victim, they will click on this link and their workstation will reconnect to my instance via a link on your site.”
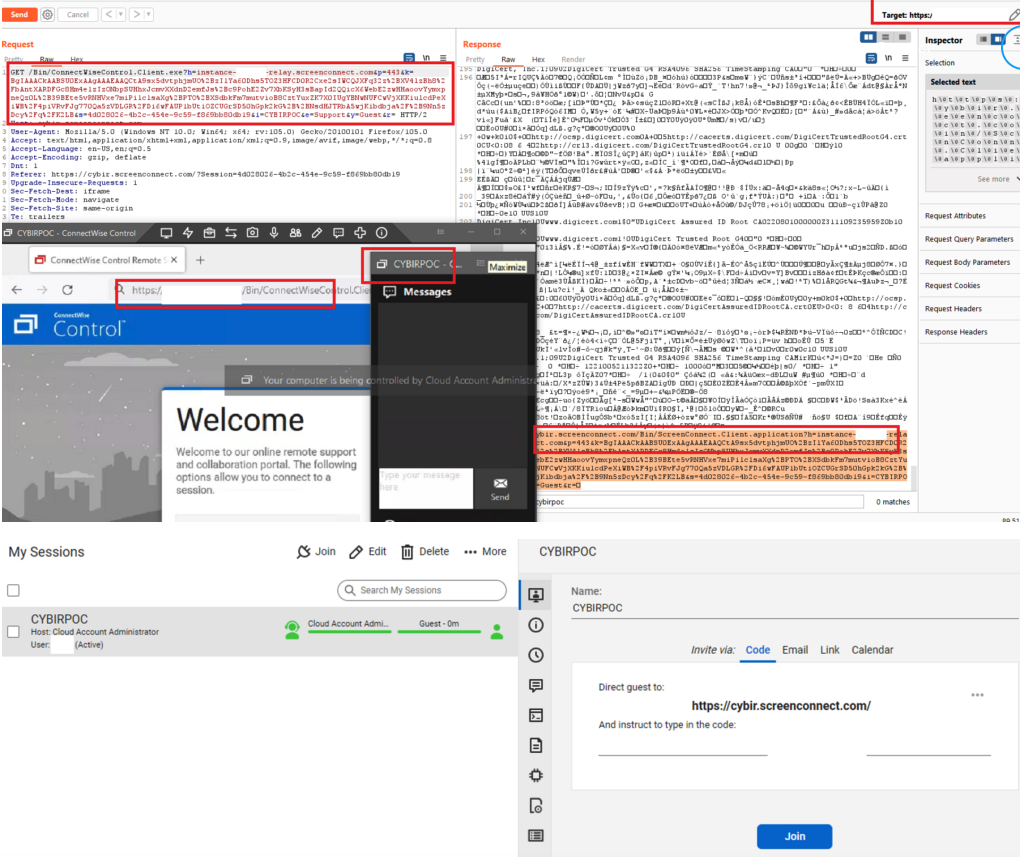
A composite of screenshots that researcher Ken Pyle put together to illustrate the ScreenConnect vulnerability.
On November 29, around the same time that Pyle posted a blog post about his findings, ConnectWise published a notice warning users to be on guard against a new round of phishing email attempts that mimic legitimate email alerts that the company sends when it detects unusual activity on a customer account.
“We are aware of a phishing campaign that mimics ConnectWise Control new login alert emails and has the potential to lead to unauthorized access to legitimate control instances,” the company said.
ConnectWise said it released software updates last month that included new protections against the misdirection vulnerability reported by Pyle. But the company said there was no reason to believe the phishers they warned against were exploiting any of the issues Pyle pointed out.
“Our team quickly triaged the report and determined that the risk to partners was minimal,” said Patrick Begs, ConnectWise’s Chief Information Security Officer. “However, the mitigation was simple and posed no risk to the partner experience, so we rolled it into the then-stable Version 22.8 and the canary of then Version 22.9, which were published through our normal publishing processes. Due to the low severity of the issue, we do not have (and do not plan to) issue any security advisories or alerts, as we reserve these notifications for serious security issues.
Beggs said the phishing attacks that triggered their notice came from an instance that was not hosted by ConnectWise.
“So we can confirm that they are not related,” he said. “Unfortunately, phishing attacks occur far too regularly across a variety of industries and products. The timing of our review and Mr. Pyle’s blog was coincidental. That said, we’re all for greater awareness of the severity of phishing attacks and the general importance of remaining vigilant and aware of potentially harmful content.
The ConnectWise advisory warned users that before clicking on any link that appears to be from their service, users should validate that the content includes “domains from trusted sources” and “links to places you recognize “.
But Pyle said that advice isn’t very useful for customers targeted in his attack scenario because phishers can send emails directly from ConnectWise, and the short link that’s presented to the user is a domain. generic that ends with ConnectWise Control’s own domain name – screenconnect .com. Additionally, examining the extremely long link generated by ConnectWise’s systems offers little information to the average user.
“It’s signed by ConnectWise and comes from them, and if you sign up for a free trial instance, you can send email invitations directly from them,” Pyle said.
ConnectWise’s warnings follow breach reports from another major remote support technology provider: Go to revealed on Nov. 30 that it was investigating a security incident involving “unusual activity within our development environment and third-party cloud storage services. The third-party cloud storage service is currently shared by GoTo and its affiliate, the password management service Last pass.
In its own notice of the incident, LastPass said it believes the intruders leveraged information stolen from a previous breach in August 2022 to gain access to “certain elements of our customers’ information.” However, LastPass maintains that its “customer passwords remain securely encrypted thanks to LastPass’ Zero Knowledge architecture.”
In short, this architecture means that if you lose or forget your all-important LastPass Master Password – the one needed to unlock access to all of your other passwords stored with them – LastPass can’t help you with that, because they do not store this. But that same architecture theoretically means that hackers who might break into LastPass’s networks can’t access that information either.
Update, 7:25 p.m. ET: Included statement from ConnectWise CISO.
ConnectWise, which offers a self-hosted remote desktop software application widely used by managed service providers (MSPs), warns of an unusually sophisticated phishing attack that can allow attackers to take control of users’ systems remotely when recipients click on the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.
A phishing attack targeting MSP customers using ConnectWise.
ConnectWise Control is extremely popular among MSPs who remotely manage, protect and maintain large numbers of computers for client organizations. Their product provides dynamic client software and a hosted server that connects two or more computers together and provides temporary or persistent remote access to those client systems.
When a support technician wants to use it to remotely administer a computer, the ConnectWise website generates an executable file that is digitally signed by ConnectWise and downloadable by the customer via a hyperlink.
When the remote user needing assistance clicks on the link, their computer is then directly connected to the remote administrator’s computer, who can then control the customer’s computer as if they were sitting in front of it.
While modern Microsoft Windows operating systems by default ask users if they want to run a downloaded executable file, many systems configured for remote administration by MSPs disable this User Account Control feature for this purpose. particular application.
In October, security researcher Ken Pyle alerted ConnectWise that its client executable is generated based on parameters controlled by the customer. This means that an attacker could create a ConnectWise Control client download link that would bounce or proxy the remote connection from the MSP servers to a server controlled by the attacker.
This is dangerous because many organizations that rely on MSPs to manage their computers often configure their networks so that only remote support connections from their MSP’s networks are allowed.
Using a free ConnectWise trial account, Pyle showed the company how easy it was to create a client executable that was cryptographically signed by ConnectWise and could bypass these network restrictions by bouncing the connection. via an attacker’s ConnectWise Control server.
“As an attacker, you have full control over the link parameters, and that link is injected into an executable file downloaded by the client through an unauthenticated web interface,” said Pyle, partner and exploit developer at Cybir security company. “I can send this link to a victim, they will click on this link and their workstation will reconnect to my instance via a link on your site.”

A composite of screenshots that researcher Ken Pyle put together to illustrate the ScreenConnect vulnerability.
On November 29, around the same time that Pyle posted a blog post about his findings, ConnectWise published a notice warning users to be on guard against a new round of phishing email attempts that mimic legitimate email alerts that the company sends when it detects unusual activity on a customer account.
“We are aware of a phishing campaign that mimics ConnectWise Control new login alert emails and has the potential to lead to unauthorized access to legitimate control instances,” the company said.
ConnectWise said it released software updates last month that included new protections against the misdirection vulnerability reported by Pyle. But the company said there was no reason to believe the phishers they warned against were exploiting any of the issues Pyle pointed out.
“Our team quickly triaged the report and determined that the risk to partners was minimal,” said Patrick Begs, ConnectWise’s Chief Information Security Officer. “However, the mitigation was simple and posed no risk to the partner experience, so we rolled it into the then-stable Version 22.8 and the canary of then Version 22.9, which were published through our normal publishing processes. Due to the low severity of the issue, we do not have (and do not plan to) issue any security advisories or alerts, as we reserve these notifications for serious security issues.
Beggs said the phishing attacks that triggered their notice came from an instance that was not hosted by ConnectWise.
“So we can confirm that they are not related,” he said. “Unfortunately, phishing attacks occur far too regularly across a variety of industries and products. The timing of our review and Mr. Pyle’s blog was coincidental. That said, we’re all for greater awareness of the severity of phishing attacks and the general importance of remaining vigilant and aware of potentially harmful content.
The ConnectWise advisory warned users that before clicking on any link that appears to be from their service, users should validate that the content includes “domains from trusted sources” and “links to places you recognize “.
But Pyle said that advice isn’t very useful for customers targeted in his attack scenario because phishers can send emails directly from ConnectWise, and the short link that’s presented to the user is a domain. generic that ends with ConnectWise Control’s own domain name – screenconnect .com. Additionally, examining the extremely long link generated by ConnectWise’s systems offers little information to the average user.
“It’s signed by ConnectWise and comes from them, and if you sign up for a free trial instance, you can send email invitations directly from them,” Pyle said.
ConnectWise’s warnings follow breach reports from another major remote support technology provider: Go to revealed on Nov. 30 that it was investigating a security incident involving “unusual activity within our development environment and third-party cloud storage services. The third-party cloud storage service is currently shared by GoTo and its affiliate, the password management service Last pass.
In its own notice of the incident, LastPass said it believes the intruders leveraged information stolen from a previous breach in August 2022 to gain access to “certain elements of our customers’ information.” However, LastPass maintains that its “customer passwords remain securely encrypted thanks to LastPass’ Zero Knowledge architecture.”
In short, this architecture means that if you lose or forget your all-important LastPass Master Password – the one needed to unlock access to all of your other passwords stored with them – LastPass can’t help you with that, because they do not store this. But that same architecture theoretically means that hackers who might break into LastPass’s networks can’t access that information either.
Update, 7:25 p.m. ET: Included statement from ConnectWise CISO.





